NIS2 in Force: What UK Businesses Trading into the EU Need to Know Now
The NIS2 Directive is no longer on the horizon — it’s here.
As of 17 October 2024, all EU Member States had to transpose NIS2 into national law. As of 22 June 2025, enforcement is underway.
If your UK-based business trades into the EU, serves `EU clients, or operates in critical sectors — this law could apply to you now.
What Is NIS2?
The Network and Information Systems Directive 2 (NIS2) is the EU’s major update to its original 2016 cybersecurity law.
This new version expands the obligations for companies operating in — or delivering services to — the EU. It covers a broad range of areas, from supply chain risks to executive accountability.
In simple terms: NIS2 raises the bar.
Businesses now need to meet defined cybersecurity and governance standards — or face serious consequences.
Why UK Businesses Need to Care
Even though the UK is no longer part of the EU, NIS2 can still apply to your business.
You may fall under NIS2 obligations if your company:
Has clients, partners, or offices in the EU
Provides services to “essential” or “important” sectors in the EU
Is part of an EU-based supply chain
Offers digital or cloud-based services to EU organisations
Key sectors include:
Energy, water, transport
Healthcare, banking, public services
Data centres, cloud providers, ICT, consultancy
Even indirect involvement — like being a subcontractor or technology provider — can trigger NIS2 requirements.
If your services reach the EU, regulators and clients may now expect you to prove your cybersecurity readiness.
Enforcement Has Started — Are You Ready?
NIS2 enforcement is already underway.
If your business falls under NIS2, you should already have recognised systems, policies, and frameworks in place.
If you’re missing any of these — it’s time to act.
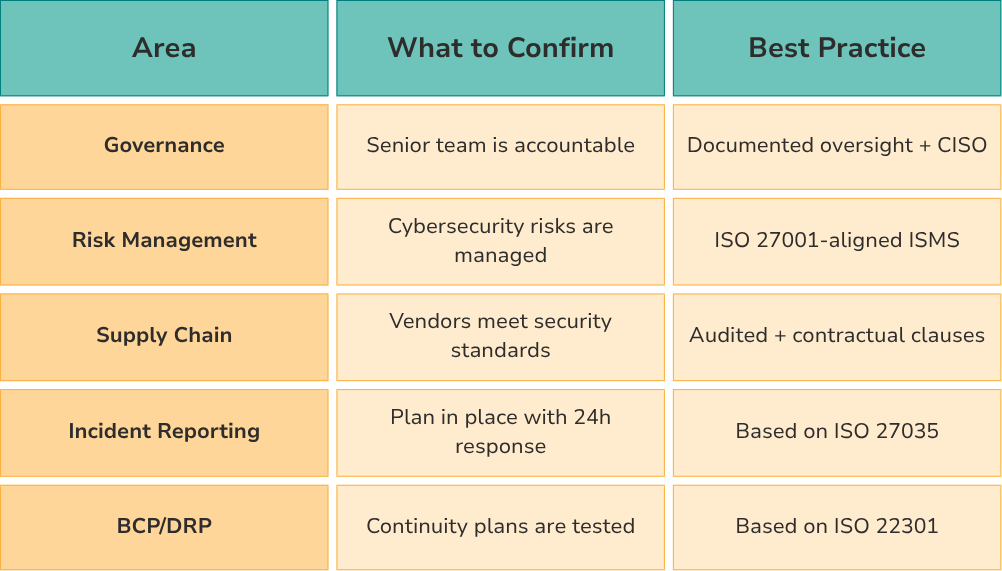
Here’s what’s required under NIS2:
1. Risk Management Framework
Standard to align with: ISO/IEC 27001
What’s required:
- Formal strategy covering network and information security
- Physical, environmental, and supply chain risks addressed
- Crisis response and continuity planning built-in
You should already have:
✔ An ISO 2700-aligned Information Security Management System (ISMS)
✔ A live Risk Management Policy
✔ Ongoing monitoring and regular audits
2. Incident Detection & Response System
Frameworks to consider: NIST Cybersecurity Framework, ISO/IEC 27035
What’s required:
Detect and report serious incidents within strict deadlines:
- Initial report within 24 hours
- Final report within 1 month
You should already have:
✔ Real-time threat detection and alerting
✔ Documented Incident Response Plan (IRP)
✔ A trained Incident Response Team (IRT)
3. Supply Chain Cybersecurity Controls
Standards to use: ISO 27036, ISO 27001 Clause 15
What’s required:
- Prove suppliers, contractors, and cloud services meet security standards
You should already have:
✔ Vendor cybersecurity assessment process
✔ Contracts with NIS2-aligned clauses
✔ Supply chain risk register and audit trail
4. Cybersecurity Governance & Executive Oversight
Best practices: Governance aligned to ISO 27001 leadership clauses
What’s required:
- Senior management held personally accountable
- Clear board-level oversight
You should already have:
✔ Named executive lead (e.g. CISO or Head of Security)
✔ Governance group or committee
✔ Evidence of board-level decisions and training
5. Business Continuity & Disaster Recovery Planning
Standards to align with: ISO 22301, ISO 27031
What’s required:
- Keep critical operations running during and after cyber incidents
You should already have:
✔ Documented and tested Business Continuity Plan (BCP)
✔ Disaster Recovery Plan (DRP) for IT infrastructure
✔ Records of tabletop exercises or simulations
What to Do If You’re Not Fully Compliant
If you’ve missed the NIS2 deadline — don’t panic, but don’t delay.
Regulators are likely to focus on your readiness and intent, not just ticking every technical box on day one.
To stay on the front foot, you should be able to demonstrate:
You understand your obligations under NIS2
You’ve started or completed a gap analysis
You have a clear plan and timeline to close the gaps
You’ve appointed responsibility internally or sought expert support
Taking visible, proactive steps helps protect your business, maintain client trust — and reduces the risk of regulatory penalties.
It’s not too late - but you have to act now.
Proactive businesses are already making moves — make sure you’re one of them.
Why This Matters
Whether you’re a digital consultancy, a service provider, or part of a critical supply chain — your reputation, contracts, and operational resilience are now at stake.
Cybersecurity isn’t optional anymore — under NIS2, it’s the law.
Failing to comply or demonstrate readiness can lead to:
Regulatory fines issued by national authorities
Lost contracts — especially with regulated EU clients
Legal claims if a data breach or service disruption occurs
Operational disruption from unmitigated cyber incidents
Reputational damage that affects client and partner trust
Being prepared isn’t just about avoiding penalties — it protects your business, your clients, and your growth.
Alignment vs Certification — What’s Enough?
You don’t necessarily need formal certification to meet NIS2 requirements — but you do need to prove your internal systems align with recognised standards like ISO/IEC 27001.
The difference?
Alignment shows intent and effort — a good start
Certification provides clear, independent evidence of compliance
For many businesses, especially those delivering digital services or operating in high-risk supply chains, formal certification isn’t just easier to prove — it’s becoming a commercial necessity.
Think of it like a seatbelt:
You can say you’re holding on — but proving it’s buckled is what keeps you safe.
NIS2 Fast Action Checklist
NIS2 is already being enforced — and for many UK businesses, proving your readiness is now essential.
By aligning your systems with recognised standards like ISO 27001, improving your risk management, and strengthening your supply chain controls, you can protect your operations and meet evolving EU expectations.
If you're unsure where your organisation stands or need support getting compliant — we’re here to help.